The site blog.chpwn.com has reported that there is a version of Carrier IQ within Apple's iOS 5.x.x. I am sure that by now you have read the reports about Carrier IQ being discovered on mobile devices by Trevor Eckhart. The analysis on blog.chpwn.com is missing some key details as it relates to iOS 5.x.x that are useful in managing any RISK. To help users make informed decisions and understand the risk involved we will provide full details related to Apple's "Diagnostic & Usage Data."
Summary
In iOS 5.x.x you do not need to Jail Break the Phone and finding the information collected does not require technical expertise. (Just have to know where to look.) What is most important to note is that the data is anonymous and users have complete control. Turning off "Diagnostics and Usage" along with System Services Location will prevent any reporting. Users can view and disable the sharing of data on their iOS device running 5.x.x at anytime. What is collected, transmitted and how a user manages the collection of data is clearly stated in Apple's "About Diagnostics and Privacy" statement.
The improvements in the management of the data can be traced back to April 2011, when it was discovered that Apple was in fact tracking users location data. The result of that discovery has resulted in Apple providing a clear and concise way in which users can manage "Diagnostic & Usage Data." So after all there is something to be said for a company being scared straight.
Checking Your Diagnostic & Usage Files and Settings
Apple iOS 5.x.x during the inital setup phase will ask the user if they would like to share "Diagnostic & Usage Data." (This is disabled by default.) If a user enables this option data about the phone including location data related to cell service will be anonymously collected and sent to Apple. It is really easy to turn this option on and off and to review the data that has been collected and transmitted if the option is enabled.
If you go into Setting>General>About>Diagnostic & Usage you are presented with the following screen. On this device below automatically send diagnostic and usage data is turned on.
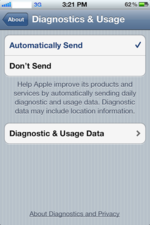 Diagnostics & UsageIf you select "Diagnostic & Usage Data" you will see a list of files the collected data if the phone had "Automatically Send" enabled at some point. The file format is awdd_<Data><Time>xxx.metriclog which is consistent with Carrier IQ.
Diagnostics & UsageIf you select "Diagnostic & Usage Data" you will see a list of files the collected data if the phone had "Automatically Send" enabled at some point. The file format is awdd_<Data><Time>xxx.metriclog which is consistent with Carrier IQ.
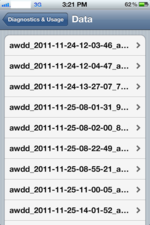 aawd File ListIn addition to crash logs and calibration information the files contain information about the iOS 5.x.x device but all device information remains anonymous. Apple clearly explains what data is collected and how a user can manage it, more on that in a moment.
aawd File ListIn addition to crash logs and calibration information the files contain information about the iOS 5.x.x device but all device information remains anonymous. Apple clearly explains what data is collected and how a user can manage it, more on that in a moment.
 awdd Example one
awdd Example one
Notice that the isAnonymous key <value is set to TRUE. You can also view all of the other key <value> pairs within the file. Cell service information at your location is collected if that option is enabled in Location Services. This data is includes cellularXXXCellInfo, channels, band, hybrid_active_channel, etc. The deviceId value is the SysInfoCrashReporterKey which does not contain information that is device specific such as the MAC address, serial number, IMEI/MEID or the ICCID. Physical access to the device or to an un-encrypted backup allows an individual access to the deviceId (theSysInfoCrashReporterKey.)
 awdd Example Two
awdd Example Two
This awdd data files also contain diagnostic information related to applications and hardware, the example below is specific to the camera.
 com.apple.camera Example
com.apple.camera Example
Turning Off Reporting of Diagnostic & Usage
Turning off the collection of "Diagnostic and Usage Files" is very easy to do, you simply select "Don't Send" in Settings>General>About>Diagnostic and Usage.
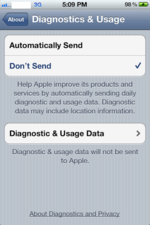 Turning Off Diagnostic and Usage DataNo data or crash logs will be shared or sent but the files created will remain on the device for a undetermined period of time (Update Pending). They also remain in any backups of any iOS device backup. If you want to achieve a zero impact foresic foot print as it relates to these files you must setup the device initially with "Don't Send" selected.
Turning Off Diagnostic and Usage DataNo data or crash logs will be shared or sent but the files created will remain on the device for a undetermined period of time (Update Pending). They also remain in any backups of any iOS device backup. If you want to achieve a zero impact foresic foot print as it relates to these files you must setup the device initially with "Don't Send" selected.
Turning Off Location Services
As stated above a major issue back in April 2011 was the discovery that Apple was collecting location data of users. Location data is a double edge sword no matter the device in question. (When it comes to mobile devices device=user.) The profile of the user predetermines all specific location settings for Applications and System Services. (For example a high value user would have a different location settings profile as compared to a low value.) At the enterprise level these can be managed with iPhone Configuration Utility.app.
If you have "Diagnostics & Usage" set to "Automatically Send" and enabled the location based services for the system service "Diagnostics & Usage" in the Settings>Location>Services>System Services window, cellular data related to your location is shared anonymously. You can turn this off in Settings>Location>Services>System Services and toggle "Diagnostocs & Usage" to off.
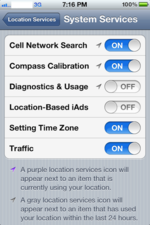 Location Services System Services
Location Services System Services
Apple's Diagnostics and Privacy
Apple has a plain language privacy policy when it comes to diagnostic data collection along with clear instructions on how to turn it off. That infomation can be found on every iOS device running 5.x.x at Settings>General>About>Diagnostics & Usage. If you click the "About Diagnostics and Privacy" on the bottom of the view the following will appear.
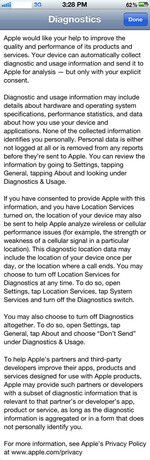 Apple Diagnostics and Privacy
Apple Diagnostics and Privacy
Facts
- iOS 5.x.x Diagnostics & Usage data is anonymous.
- iOS 5.x.x Diagnostics & Usage data reporting can be turned off.
- iOS 5.x.x is Diagnostics & Usage data uses SysInfoCrashReporterKey as a key<value> for the deviceId flag, thus with physical access to the device you can obtain this number.
RISK
Poor management, limited knowledge and misleading information represent the Highest Degree of RISK related to iOS 5.x.x "Diagnostic & Usage" reporting.
iOS 5.x.x "Diagnostic & Usage" RISK can be mitigated with management of your iOS settings.
The RISK to user privacy is LOW in iOS 5.x.x as it relates to "Diagnostic & Usage" reporting.
Mitigation
Individual user or system profile must determine all Applications and System Services specific location and "Diagnostic & Usage" reporting settings.
It is not recommended to provide any "Diagnostic & Usage" data or location data for any high value system or user.
General users should consider disabling "Diagnostic & Usage" reporting and turn off location services for this system service. Residual risk remains such as interception and physical access compromise thus consider additional mitigation.
Addition Mitigation
- Encrypt all Backups of iOS devices on your Computer.
- Use a Passcode of Significant strength.
- Enable Find My iPhone if appropriate.
- Ensure that Mobile Wipe is available.
Additional Notes
Test done on iPad 2 and iPhone 4s running iOS 5.0 and 5.0.1. Due to our specific privacy policiy some information has been removed. To contact us please use the following form here.
 Saturday, March 17, 2012 at 08:29AM
Saturday, March 17, 2012 at 08:29AM  Figure 1: Warning Dialog for downloaded Application from Internet
Figure 1: Warning Dialog for downloaded Application from Internet Apple,
Apple,  Decoy,
Decoy,  Fake,
Fake,  Limited Risk,
Limited Risk,  Mac OSX 10.7.x
Mac OSX 10.7.x