Saturday
Mar172012
Imuler.C Uses Icon Decoy method- LOW RISK
 Saturday, March 17, 2012 at 08:29AM
Saturday, March 17, 2012 at 08:29AM Imuler.c, reported by Intego, is a low risk icon decoy social engineering attack. In MacOSX the user you can simply copy an icon to another file by using "File>Get Info (Comand-I)" in the Finder.
Summary
Within a zip file the criminals hide an Application with an icon that looks like an image along with other image files. The decoy is an attempt to get the user to click on the Application and run the malicious file.
FACTS
- This is a social engineering attack based on an attack method dating back to Mac OS 7 (Pre-OSX).
- The stratergy of the attacker is Icon Decoying.
- Users can turn on view extensions or use detail list to see the file type. (This is not really needed.)
- MacOSX will prompt the user if they try to open a file for the first time downloaded from the internet.
- You need to be the administrator to install or run the malicious application. Enterprise managers should manage these options in Mac OSX.
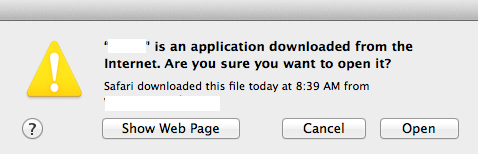 Figure 1: Warning Dialog for downloaded Application from Internet
Figure 1: Warning Dialog for downloaded Application from Internet
RISK
Imuler.C as all of it's previous versions are VERY LOW RISK. The attack method is similar to the PDF decoy in September 2011. The Application with the Icon Decoy is an attempt to use tactics decades old.
MITIGATION
- Do all your computing as a general user, not the administrator. This stops most malicious installers in there tracks.
- Do not open files from un-trusted sources.
- Make sure that if you open an Application that you downloaded that you confirm the (HASH).
- When you first open a file downloaded from the internet you will recieve the dialog in Figure 1, make sure that you trust that application.
- Optional : Turn on "Show all applications extensions" in Finder>Preferences>Advance.
- Enterprise administrator can manage what applications user can and cannot run.
- Enterprise adminstrators should rely on the priciple of least privileged for application exectuion for users.
in  Apple,
Apple,  Decoy,
Decoy,  Fake,
Fake,  Limited Risk,
Limited Risk,  Mac OSX 10.7.x
Mac OSX 10.7.x
 Apple,
Apple,  Decoy,
Decoy,  Fake,
Fake,  Limited Risk,
Limited Risk,  Mac OSX 10.7.x
Mac OSX 10.7.x 






