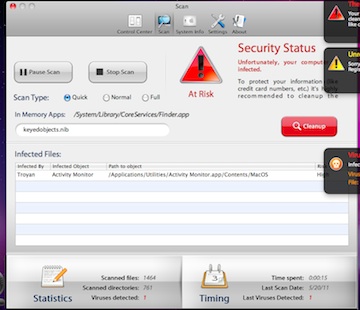
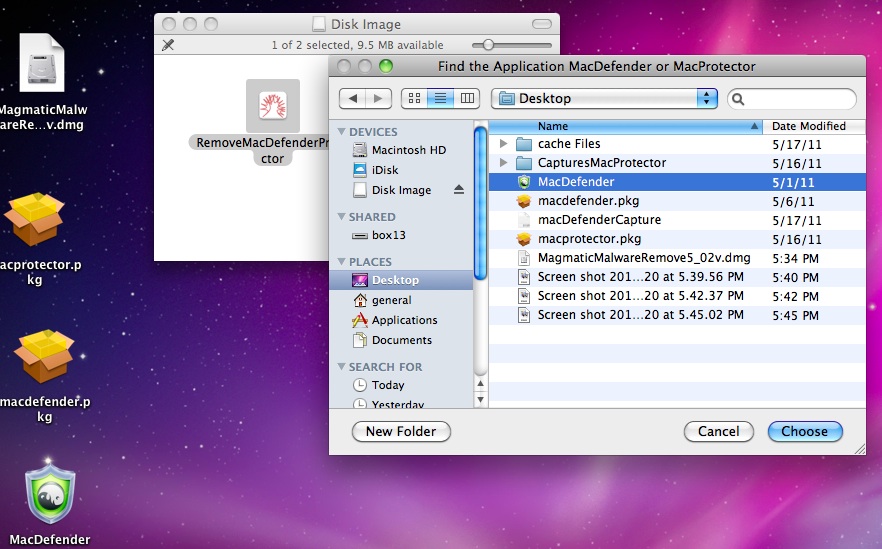
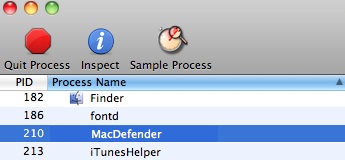
That recent malware that targeted Mac OSX systems, MacDefender and MacProtector, are fake anti-virus products designed to steal users personal information including credit card accounts. We think version OSX/MAcDefender.F tries to steal two credit card numbers by bouncing one and directing the user to another site. Below is our pending draft analysis for OSX/MacDefender.A , OSX/MacDefender.D and OSX/MacDefender.F.
Our analysis includes takeaway’s of the evolution of key inherited traits within each rouge application followed by an detailed technical breakdown or the woking three variants we have. Our format is broken into stakeholder sections for executives, users, researchers and experienced MacOSX administrators. This report is a draft and may change without notification.
Excerpts From Our Analysis
Files
/Contents/MacOS/MacDefender (OSX/MacDefender.A)
MD5(MacDefender)= 2f357b6037a957be9fbd35a49fb3ab72
SHA(MacDefender)= 470e1c99d7b5ec6d00b26715f4fa37bc70984fb4
/Contents/MacOS/MacProtector (OSX/MacDefender.D)
MD5(MacProtector)= 1f8e9cd3f0717a85b96f350e4f4a539a
SHA(MacProtector)= 361ba7b420e1a9ec0af5f7811e84dc95d04624a9
Added 05_21_2011
/Contents/MacOS/MacProtector (OSX/MacDefender.F)
SHA(MacProtector)= a94bd6a52bcb275a8ff1cd15977167f709b7ab04
UPADTE PENDING
MacProtector (OSX/MacDefender.F)
It is our theory that this version of MacProtector will trick the user into to providing two credit card numbers by directing them to two separate sites. It also can ensure that if one site is down the other will continue to steal credit cards.
//
@interface URLMaster : NSObject
{
}
+ (id)getBuyPageIP; // IMP=0x000000010000f1f7
+ (id)getBackupBuyPageIP; // IMP=0x000000010000f1e8
+ (id)getSoftInstallLink; // IMP=0x000000010000f391
+ (id)getBuyPagLink; // IMP=0x000000010000f30d
+ (id)getBackupBuyPageLink; // IMP=0x000000010000f289
+ (id)getSendTicketLink; // IMP=0x000000010000f0a8
@end
@interface URLMaster : NSObject{}
+ (id)getBuyPageIP; // IMP=0x000000010000f1f7+ (id)getBackupBuyPageIP; // IMP=0x000000010000f1e8+ (id)getSoftInstallLink; // IMP=0x000000010000f391+ (id)getBuyPagLink; // IMP=0x000000010000f30d+ (id)getBackupBuyPageLink; // IMP=0x000000010000f289+ (id)getSendTicketLink; // IMP=0x000000010000f0a8
@end
- Both installers have the "ru.lproj" indicating the developer spoke Russian.
- Localizations for .nib files set to English.
- Localizations for application set to English.
- Xcode build for both was 10M2518, Xcode 3.2.6 / iOS SDK 4.3 gm which include Russian and English.
- The build machine which created both was running OSX seed 10J869, 10.6.7.
- Minimum system version is 10.5.
- Both use “df -lg|awk” to get disk space information.
- Both create and then write the output to a file named dmem.txt in the users ~/home folder
- Both use “ps -e|awk” to get process information.
- Both create and then write the output to a file named proc.txt in the users ~/home folder.
- Both use random number to seed timers, determine time to indicate infected file. (int)GetRndNum:(int)arg1:(int)arg2;
- Both use a method (void)setTimeIntervalForFirstVirAppearing to set the random time for first fake indication of virus to appear.
- MacProtector has a superior coding operating structure as compared to MacDefender.
- MacDefender opened the default browser to make a purchase, MacProtector has the Webkit framework opening a WebKit container to a site all built into the application
- MacDenfender link is dead, MacProtector link is still active remains active.
- MacDefender connect to 69 50 214 53 using default browser. (Site offline.)
- MacProtector connect to a nginx server 91 213 217 30. (Web and Reverse proxy)
- MacProtector manages and obfuscates the IP address but the serial numbers are still stored in plain text, MacDefender does not obfuscate the site IP address.
- MacProtector @Interface RegWindow handles the registration process, for example http : //91 213 217 30 / js / payform3 .js (Do not visit this link.)
- MacProtect uses token and cookies in the false activate product process.
- MacProtector uses various class methods to get ip address and confirm cookie from site.
- MacProtector sends data to 91 213 217 30.
- MacProtector receives cookies from 91 213 217 30.
- MacProtector uses methods (void)createURLForSerialNumberCookieSearch; and (void)OnCheckCookieForRegkey; to handle checking for registration cookie.
- MacProtector has a text file in resources called ksms.txt which contains the number “4”.
- MacProtector’s post flight script does not “reveal” the application in the Finder and does not use AppleScript.
Downloads-DRAFT
Update-Draft report v2.
Magmatic_Analysis_MacDefender_MacProtectorv2Draft.pdf (MAJOR UPDATE PENDING)
SHA(Magmatic_Analysis_MacDefender_MacProtectorv2Draft.pdf)= 72b17c4250da23ae3c744fb26508d2b1889ae49e
Draft report v1
Magmatic_Analysis_MacDefender_MacProtector(DRAFT)
sha=5a708a3751c3ddd7bf38fcf240d8abc676514452
Magmatic_Analysis_MacDefender_MacProtector(DRAFT)
sha=c20f74b6eef02667033ddf50ff8a4ef1a10c7f13
Class Diagrams
MacProtector (OSX/MacDefender.A)
OSX_MacDefender.A_ClassDiagramDraft2.pdf
SHA(OSX_MacDefender.A_ClassDiagramDraft2.pdf)=d4b9902967f842773a563b215cae49ac5d3bde40
MacProtector (OSX/MacDefender.D)
OSX_MacDefender.D_ClassDiagramDraft2.pdf
SHA(OSX_MacDefender.D_ClassDiagramDraft2.pdf)= 2a92c951b9378d2370d559cbcbce873660fcc12d
MacProtector (OSX/MacDefender.F)
OSX_MacDefender.F_ClassDiagramDraft2.pdf
SHA(OSX_MacDefender.F_ClassDiagramDraft2.pdf)= 2b80717c46157cd2606dcbe6a7817e5993fb7ace
Class Dumps
MacDefenderOSX_MacDefender_A_ClasssDump (OSX/MacDefender.A)
SHA(MacDefenderOSX_MacDefender_A_ClasssDump.txt)= 5087f008da46bdd3cfacaf1be9d3729f19916f65
MacDefenderOSX_MacDefender_D_ClasssDump (OSX/macDefender.D)
SHA(MacProtector_OSX_MacDefender_D_ClassDump.txt)= a53cc5a8c9cd2f19726e56beed8b07a097d7b8e2
MacDefenderOSX_MacDefender_F_ClasssDump (OSX/MacDefender.F)
SHA(MacProtector_OSX_MacDefender_F_ClassDump.txt)= f26c0091ab26b1ca998d8f58e9ee133d967c5bd8
**Note-This is draft data and contains raw information, final release of the document and addition updates will be located at here. All information is provided as is and falls under the copyright located on this site and within the draft report. Any questions use the Contact Us Link and put "MacDefenderProtector Report" in subject line.
 Friday, May 20, 2011 at 04:28PM
Friday, May 20, 2011 at 04:28PM