Recently F-Secure has reported they may have come across a Mac Trojan. The operative word being "may" from their original post which was not picked up by additional press accounts. (F-Secure is a five start organization, not that they cannot make errors but they are a gold standard when it comes to accurate disclosure.)
This PDF Decoy Malicious Installer is actually an attempt to use tactics found on the Windows platform by sending rouge documents that an unsuspecting user will open up. The taxidermy of the Windows attack attempts to execute a malicious application, open a malicious site or exploit a vulnerability in the Adobe Product line or Microsoft's Product line. In this particular case targeting Mac OSX there are very important key differences.
This is not a TROJAN running from a PDF taking advantage of an exploit or vulnerability. It is NOT EXPLOITING ANY KNOW FLAW at all, it is however using a host of deceptive tactics. It is a rouge Package Installer that installs and opens a PDF DECOY to cover up the installation of an additional services (Apache) without getting the user suspicious. In it's current form it is the technical equivalent of putting a square peg into a round hole.
How it Works
The PDF Decoy Rouge Installer PACKAGE runs additional scripts after the decoy is installed and opened up on screen. Using combinations of Preinstall scripts, Post Install scripts and/or Actions within the Package the scripts will attempt to install and/or download additional services. (We have encountered a version which installs apache.) The developer of this malicious package has attempted to use an application which cleans itself up, similar to the one used in latter version of MacDefender, AVRunner. (Class Diagram) The good news is that a properly configured Mac will mitigate this PDF Decoy Installer. This represent a LOW RISK threat in its current form.
Reports of Changing Extensions to Execute PKG Files are WRONG!
If you change the extension of a file in Mac OSX to one that it is not compatible with it will not execute or open. For example, a DMG, MPKG or PKG file that has had its extension changed to .PDF it WILL NOT open or execute. What will happen is that an error will be generated.
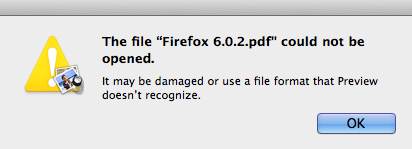 Fig. 1.1 Firefox DMG file extension changed to .PDF
Fig. 1.1 Firefox DMG file extension changed to .PDF
Primary Mitigation
Currently XProtect has been updated and will recognize this installer. In Apple Menu>System Preferences>Security & Privacy Make sure to have "Automatically update safe downloads list" Enabled for automatic updates of XProtect. (If you toggle this option it will update but make sure to do a "Show All" to save your settings. Advanced users can update XProtect manually** by doing the following:
- Open /Applications/Utilities/Terminal.app
- Type sudo /usr/libexec/XProtectUpdater
- Enter the Adminstrator Password
- Quit out of Terminal.app
It is important to realize that a developer can bypass the need for the user to enter the Administrator Password when creating an installer Package. The best defense is not to perform general computing as an administrator. This will limit what and where files can be installed. The administrator account type in Mac OSX is the equivalent of root and has full rights to install and write to a host of directories. You must use a standard user account for all your computing.
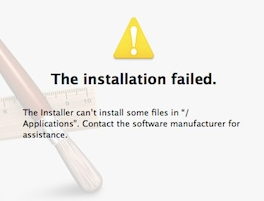 Fig. 2.1 Installer Failing Standard User Account
Fig. 2.1 Installer Failing Standard User Account
In larger deployments of Mac OSX systems protect the administrator account as you would root using layered administrative permissions and sudo to execute system altering commands. (Administrator's should never have full access to root privileges and all activities should be audited.)
Mac OSX System
- In Apple Menu>System Preferences>Security & Privacy Make sure to have "Automatically update safe downloads list" Enabled thus setting up automatic updates of XProtect.
Safari
- Do not install any program from an installer opened directly from the Web.
- Make sure "Open Safe Files" is de-selected in Safari Preferences.
- Download files only to the Download folder that is in each users home directory.
- Set Remove Downloads to "When Safari Quits." Manually clear this folder for other Browsers.
- Make sure that "Block Pop-Up Windows" is on.
- Never do Web Surfing as the Administrator, carry out daily task as a user that does not have administrator privileges.
For Chrome
- Select "Clear Auto-Opening" settings in chrome://settings/advanced.
- Never do Web Surfing as the Administrator, carry out daily task as a user that does not have administrator privileges.
Secondary Mitigation
- We also recommend that you only install Applications that come from trusted sources or from the Mac App Store. These are digitally signed so their is trace back to the developer.
- Consider installing an Anti-Virus product. We love F-Secure and Intego.
RISK
The RISK related to this PDF Decoy Malicious Installer is LOW.
We continue to monitor how this evolves since the tactics are similar to larger scale Phishing attacks designed to create a beach front into an sensitive internal systems of high profile organizations. Due to recent system updgrades at previously targeted companies of users in certain departments and groups to Mac OSX systems, these actors are attempting to discover how to use their old tactics to create new jump off points to internal compromises.
**Apple does not recommend doing this from the command line and users should consider the risk. For the general user setting the system preferences should suffice. This solution is ideal in larger managed environments.
 Saturday, March 17, 2012 at 08:29AM
Saturday, March 17, 2012 at 08:29AM 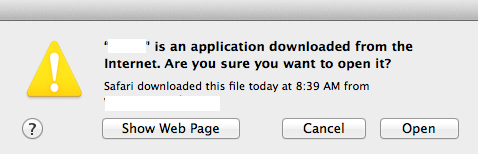 Figure 1: Warning Dialog for downloaded Application from Internet
Figure 1: Warning Dialog for downloaded Application from Internet Apple,
Apple,  Decoy,
Decoy,  Fake,
Fake,  Limited Risk,
Limited Risk,  Mac OSX 10.7.x
Mac OSX 10.7.x 








