Java Hardening Tips
 Thursday, February 23, 2012 at 07:43PM
Thursday, February 23, 2012 at 07:43PM Background
Reuse of code in crimeware kits and tools targeting Windows infrastructure via Java has been building momentum. Java is a cross platform environment which can allow criminals to take advantage of systems regardless of operating system. For example, much of the crime ware kit call BlackHole RAT is still written in Java and Real Basic. Flashback Mac Trojan as well uses Java as the gateway to compromise. We still consider the Java Threat a Low Risk since you can turn it off or manage it.
It is our thinking that because of JAVA's cross OS nature and Apple's custom update cycle, it continues to be the attack vector platform of choice. Currently Java is not included with Lion and there are few useful Java Applets for the standard Mac OSX User.
No matter the case there are a host of easy ways to eliminate the RISK or reduce it from a host of Java attack vectors including the use of a self signed certificates.
Turn Jave off to Eliminate any threats from malicious applets
If you do not need or use Java than disable it.
- In Safari goto Safari>Preferences>Security and disable Java.
- In Chrome visit Chrome://plugins and disable Java.
- In Firefox Tools>Add-ons>Plug-ins and disable Java.
Need Java
The most important setting to remember is that if you need Java make sure that you update Mac OSX to the latest version. Make sure that System Preferences>Software Update>Scheduled Check is set to check for updates daily.
Many users do not realize that the Mac OSX version of Java has a great utility called Java Preferences.app which allows you to configure how Java behaves. This includes how applets that are self signed are handled, sandboxing, checking blacklist and using CRL. Depending on the version of Java Installed, these settings may be differ.
SUGGESTED SETTING IN THE JAVA PREFERENCES.APP TO PROTECT YOUR MAC
- In /Applications/Utilities/Java Preferences.app disable "Allow User to grant permissions to content from an untrusted authority."
- In /Applications/Utilities/Java Preferences.app disable "Use certificates and keys in browser keystore" (Update-Dependent on Business needs.)
- In /Applications/Utilities/Java Preferences.app disable "Use personal certificate automatically if only one matches server request." (Update-Older Versions)
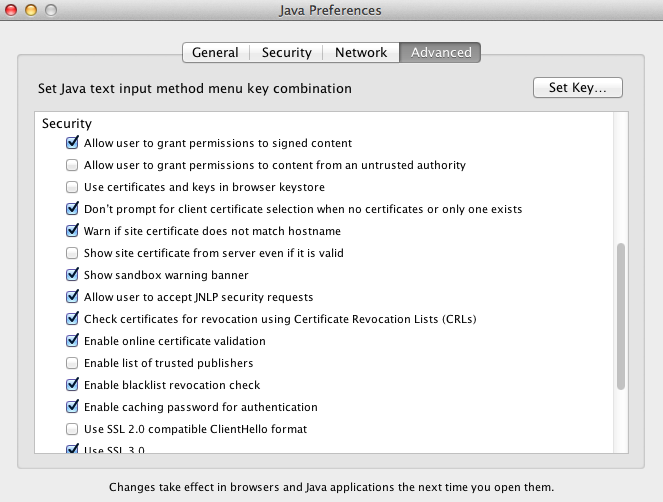 Fig. 1 Security Settings Example
Fig. 1 Security Settings Example - In /Applications/Utilities/Java Preferences.app enable "Enable blacklist revocation check."
- In /Applications/Utilities/Java Preferences.app enable "Check certificates for revocation using CRL"
- In /Applications/Utilities/Java Preferences.app enable "Enable online certificate validation"
- In /Applications/Utilities/Java Preferences.app enable Verify mix security code. "Enable-don't run untrusted code, no warning." **This should be reviewed based on business needs.
- Review Trusted Publishers in Security pane.
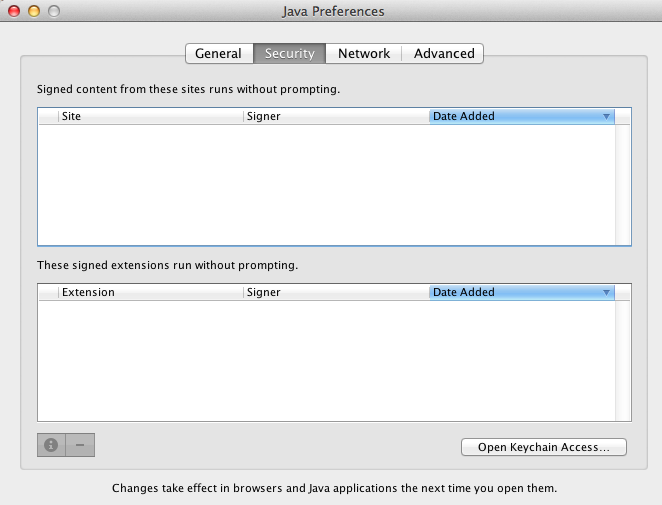 Fig.2 Security Pane Publishers
Fig.2 Security Pane Publishers
Java Preferences.app also allows the user control over the cache and storage space used. You can also review and set proxy setting for Java by selecting the Network Setting button.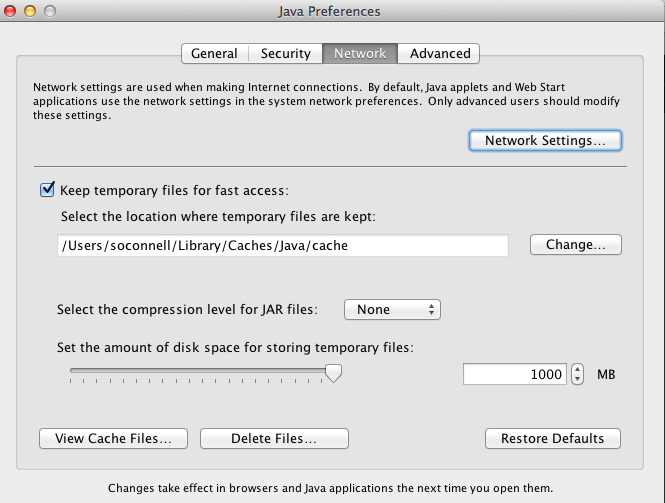 Fig 3 Java Cache Settings
Fig 3 Java Cache Settings
Consider each option based on your specific business needs. For example, if you are developing jar/applets internally consider reviewing of the signing process to insure that all internal app/jar used for production systems and properly signed by your organization.
Conclusion
Java is no longer included with Lion and we recommend disabling it in Safari, Chrome or Firefox. If you need to use Java make sure that it is up to date with the latest version from Apple using Software Update. Administrators and users can set various options in Java to manage any risk from rouge applets.
 Best Practices,
Best Practices,  How-To,
How-To,  Java
Java 






