Condition Remains GREEN
 Friday, August 30, 2013 at 03:45PM
Friday, August 30, 2013 at 03:45PM A denial of service (DOS) condition exist within CoreTEXT API. When a specific combination of Unicode characters are loaded in an application, for example one based on WebKit, the application will crash. The combination impacts a host of applications on Mac OSX and iOS including Safari, Chrome, Twitter, Mail and TextEdit. (Any application dependent on CoreText API.)
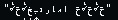
Currently there is no exploit related to the crash. Each application handles the Text Encoding in Mac OSX, thus the settings are application dependent. You should only make changes if you encounter a DOS condition related to the character set. iOS7beta and Mavericks beta are not impacted.
Mitigation In Safari
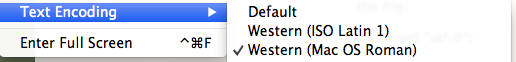
- Change the Text Encoding in Safari
Set View>Text Encoding to Western (Mac OS Roman) <@charset "macintosh"> if you encounter this error. The offending page wil then load.
Mitigation In Text Edit
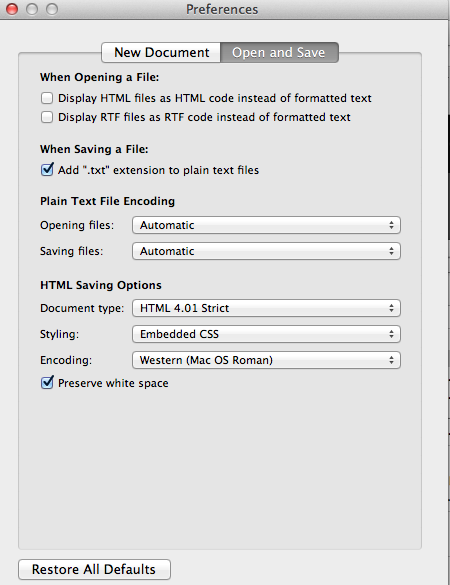
- Change the Text Encoding in Text Edit if you encounter the error.
TextEdit>Preferences>Open and Save>Encoding>Mac OS Roman
Individuals are creating a DOS condition on sites by pasting the combination in to comments. Several providers have limited users from being able to post the combination including Facebook, Twitter and Google. iOS 7 Beta and Mac 10.9 Beta currently are unaffected
 Condition:GREEN
Condition:GREEN