Condition Remains GREEN
 Friday, August 30, 2013 at 03:25PM
Friday, August 30, 2013 at 03:25PM Rapid7 has release a Vulnerability notice for CVE-2013-1775 which under specific conditions a user can gain super user using the "-k" option of the sudo command. There is little risk from this exploit, hence why Rapid7 released it. When using the sudo command there is a default time before the environment resets resulting in an authentication time out. You can adjust the defaults using visudo. You should always do basic computing as a non-administrator which limits the risk from this kind of privilege escalation.
Summary of Conditions to be Effective
- The user must be in the Administrator group, basically an administrator.
- The user must have run the sudo command, in the /etc/sudoers file. (Note-group execution bit.)
- sudo authentication must not have timed out. (Important for Servers with custom /etc/sudoers)
- sudo -k option flaw reliant on settings in /etc/sudoers.
Primary Mitigation For All Users
These trivial mitigation steps prevent changing the System Time thus making the vulnerability ineffective.
- Make sure that "Set date and time automatically is on" in System Preferences>Date &Time. (Critical setting to mitigate.)
- Make sure that "Require an administrator password to access locked preferences" in on in Security & Privacy>Advance. (Critical setting to mitigate.)
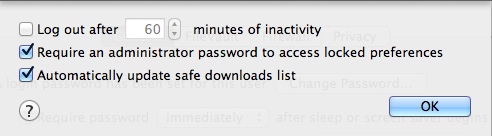
- Make sure that system preference "Click lock.." is set to LOCK. (Critical setting to mitigate.)
Mitigation For Advanced Configurations
These Mitigation methods can be useful for Sever Administrators in a complex server environment.
- Do not do general computing as an administrator account.
- Make sure that "Set date and time automatically is on" in System Preferences>Date &Time. (Critical setting to mitigate.)
- Make sure that "Require an administrator password to access locked preferences" in on in Security & Privacy>Advance. (Critical setting to mitigate.)
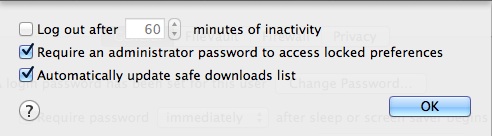
- Make sure that system preference "Click lock.." is set to LOCK. (Critical setting to mitigate.)
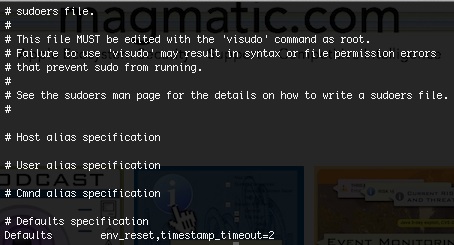
- You can alter sudo timeout using visudo, this long with a host of other setting . For example you can set the default sudo timeout (env_reset defaults) to 2 minutes using the "timestamp_timeout" variable. See man page for more options. (Advanced & Server users..)
- Set Require password immediately.
- Enterprise users should audit privileges, set restrictions in /etc/sudoers, review group and user execution bits for critical files related to sudo.
For more information visit the man page for sudo, visudo.
 Condition:GREEN
Condition:GREEN 






